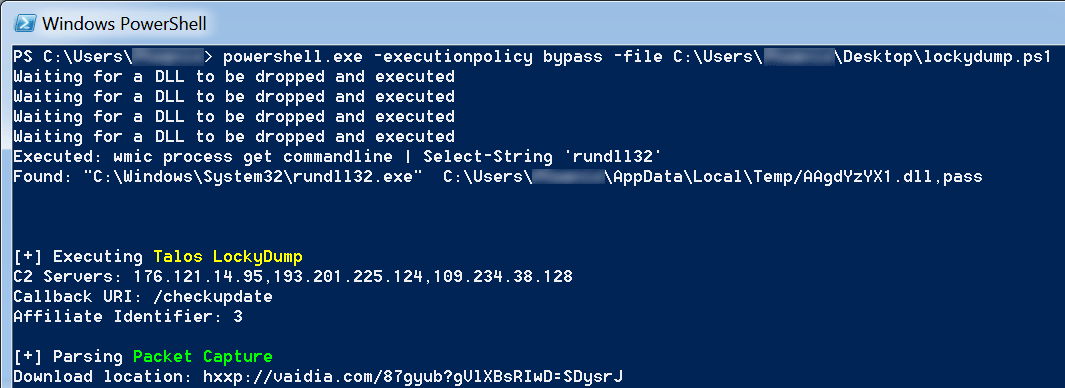
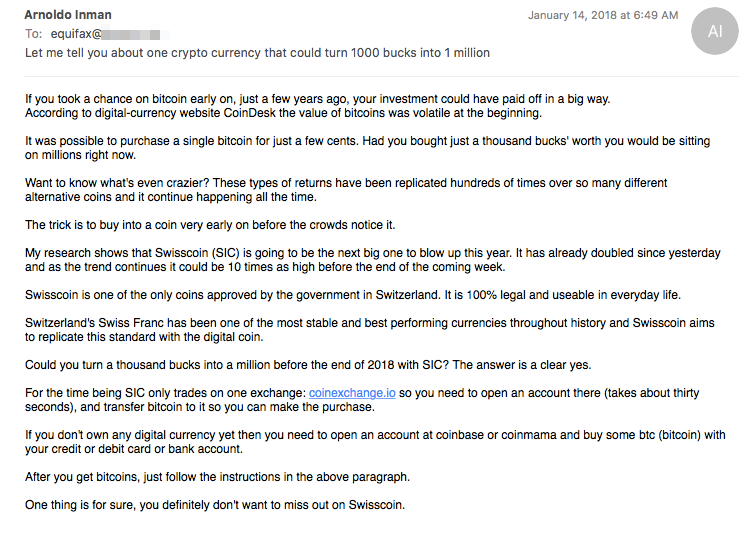
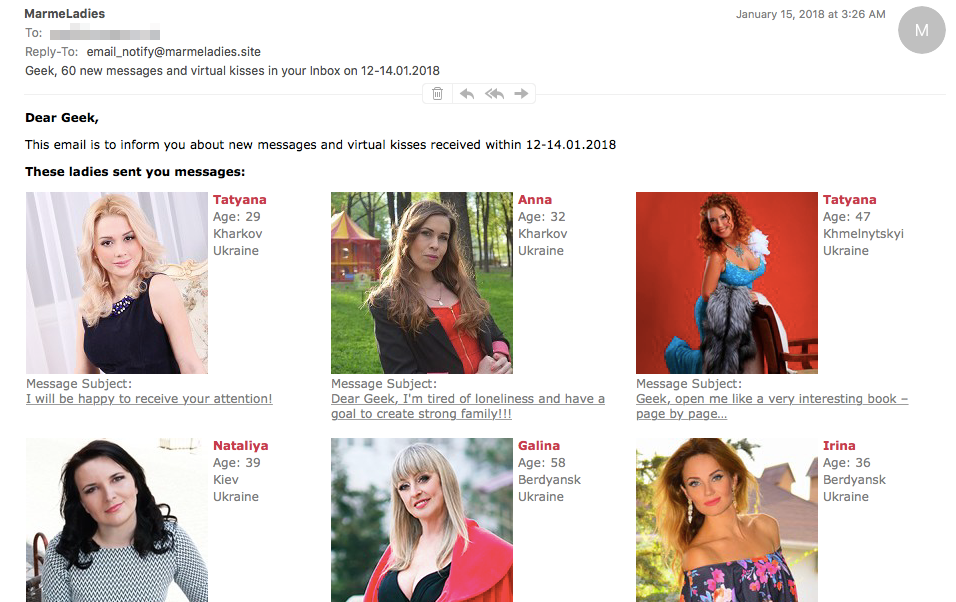
The Necurs botnet is a distributor of many pieces of malware, most notably Locky.
Reports
Around June 1, 2016, the botnet went offline, perhaps due to a glitch in the command and control server running Necurs. However, three weeks later, Jon French from AppRiver discovered a spike in spam emails, signifying either a temporary spike in the botnet's activity or return to its normal pre-June 1 state.
In a 2020 report, it was noted to have particularly targeted India, Southeast Asia, Turkey and Mexico.
Distributed malware
Source:
- Bart
- Dridex
- Locky
- RockLoader
- Globeimposter
See also
- Conficker
- Command and control (malware)
- Gameover ZeuS
- Operation Tovar
- Timeline of computer viruses and worms
- Tiny Banker Trojan
- Torpig
- Zeus (malware)
- Zombie (computer science)
References